Indian ISP ACT Fibernet blocks bit.ly. Does DNS Hijacking

TLDR;
Indian ISP ACT Fibernet (aka Beam Telecom) hijacks its users’ DNS requests (even when using public DNS servers like Google or OpenDNS) and blocks websites through this method. This has huge implications beyond website blocking and you can’t rely on anything that you are browsing anymore though there are ways available to make yourself safe.
Aside: Indian ISPs are blocking benign/collateral damage sites now like bit.ly for ACT and behance.net for Airtel. Pretty soon most of web will be blocked in India at this rate.
Update: It seems that some folks on ACT do not see the block/DNS hijack. So far, they all seem to be on dynamic IP. It could be either that the hijacking is being done only for static IP folks or for specific IP ranges. Please comment here or tweet to me @shantanugoel if you are on ACT but do not see the block and/or dns hijack.
Update 2: Got a call from ACT team and they’ve unblocked bit.ly this morning. However, DNS hijacking, the primary problem, still seems to be there for many users.
The Whole shebang#
URL/website blocking is not new in India and ISPs causing it show up in weird ways is not new as well like we saw not too long ago:
So, we figured this out finally. @CloudFlare is not really doing an MITM here but getting MITM'ed by airtel https://t.co/Htild9sWIv
— Shantanu Goel (@shantanugoel) July 13, 2016
We’ve come to expect such things happen already for sites which may host pirated content like TPB and other torrents sites, etc. But “shocked” or “surprised” would be understatements of what I felt when I saw that a generic url shortener like bit.ly was blocked as well. All I was trying to see was a benign backstory about CitrusPay founders shared by someone on twitter and BAM!
Now, bit.ly has been blocked in India. FML. Block everything. Block the internet itself BC. pic.twitter.com/e5MFLVXIao
— Shantanu Goel (@shantanugoel) September 17, 2016

Something bigger than blocking#
But the rage didn’t stop at this.
I tried the usual way of adding “https” to bypass the block but it was highly unusual to see another error which said bit.ly closed my connection. I was sure bit.ly supports https as I could see on my Airtel connection. So this was weird.
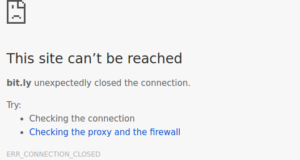
I tried a simple ping to bit.ly and well well well! It turns out, I am not even connecting to bit.ly at all but one of the servers of my ISP itself. The other sites like google.com were being resolved correctly.
Well, I'll be damned :o bit.ly is pointing to https://t.co/Yp6tdKp23o pic.twitter.com/thTD2dvEv3
— Shantanu Goel (@shantanugoel) September 17, 2016
This “might” have been okay/explained away if I was using my ISP’s DNS servers (even though it’d be unethical in my book even then). But I was NOT using ISP’s DNS servers in the first place (who does that, seriously?).
I was using google’s public DNS servers at my router as well as PC level and resolve.conf is set to use localhost. So I was pretty sure I am using the google dns and I shouldn’t have got a fake IP back. This was an even bigger red flag!
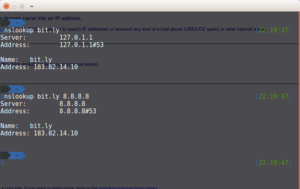
I ran the nslookup on bit.ly through an online service and it gave me the correct bit.ly server IPs but running nslookup on my PC or even on my router gave me back the fake IP.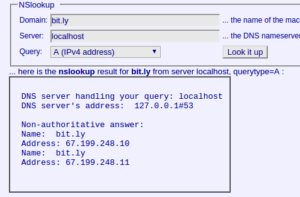
Transparent DNS Proxy / DNS Hijacking#
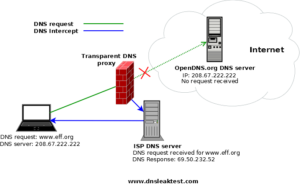
This is how (bad) ISPs do this. They look for all traffic on port 53 (the DNS port) and don’t let them go to the actual DNS server and fulfill it from their own DNS servers, thus forcing you to go to a location of their bidding.
In my case, I tried running the various “DNS leak tests”/“Transparent Proxy detection” tests but they all came out fine. Because my ISP is doing something clever here. I am assuming that they look at all the addresses that you are trying to reach, and then serve the ones they are interested in from their servers while passing on the rest of the requests to your originally intended dns server.
How these tests work is that they see your IP, then ask your browser to connect to some specific server (like 7325abcd.mydnsleaktest.com) and see the IP which is actually touching their dns servers to query that address. I looked at these results and they all showed google to be the one connecting to them and so that seemed fine.
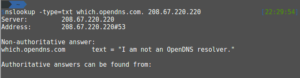
Luckily, my ISP is not doing this (cannot do this?) for the opendns test and it detected the proxying immediately.
Implications/How to protect yourself#
The situation is grim now because your ISP can control everything you visit on the internet and you wouldn’t even know. You could be sending all your searches to your ISP, giving your passwords to them through fake sites, or they could silently replace the script/css etc servers and track all of your behavior, the implications are endless.
But all is not lost. There are a few ways to protect yourself from this:
Add the IP manually to your hosts file: (H/T https://twitter.com/electron0zero). This is the simplest way as it will bypass even connecting to DNS server at all. But is cumbersome as you have to manually add each site and also update it if the IP changes.
Get a VPN. I prefer this the least though because it is expensive, slow, and in general problematic to setup everywhere.
**Reroute your DNS requests to some other non-standard port. **You will need to have a bit of iptables know-how for this and a router good enough to give you this access. But your ISP can’t (?) monitor every port for DNS traffic. Theoretically they could though.
Use DNSCrypt. This is my recommended method and what I chose to save myself. This is good in future as well to save you from other DNS attacks. From DNScrypt.org
DNSCrypt is a protocol that authenticates communications between a DNS client and a DNS resolver. It prevents DNS spoofing. It uses cryptographic signatures to verify that responses originate from the chosen DNS resolver and haven’t been tampered with.
Depending on your machines/routers, it can range from easy to difficult. On my Asus RT-N66U with custom firmware, all it took was one line of opkg command to install it and another few lines to start it up at boot and configure dnsmasq to use it.
Closing#
It’s not closed yet. I am talking to my ISP to figure this out and see if they will accept removing this kind of malpractice (I don’t think they will. But one has to try!). Please do share this to raise awareness. If you have any queries or any other information about this, please do get in touch with me on @shantanugoel
As an aside, this also means that there is an order out to block bit.ly as well and other ISPs may follow suite soon :|